'Codes and Ciphers' Puts Students to Test
Math course offers insight into creating and solving secret messages.
At their simplest, they are used by kids passing notes in class and at their most complex, by governments carrying out military operations. In between, they are used by people every time they pull out a credit card or shop online.
Codes substitute arbitrary symbols—typically, letters or numbers—for the components of the original message. Ciphers use algorithms to transform a message into an apparently random string of characters.
In “Codes and Ciphers,” a special topic course offered recently by the mathematics department, students learn the difference and get an introduction to classical and modern methods for encoding secret messages (cryptography) and the science of breaking codes and ciphers (cryptanalysis). It blends the history of secret writing, the art of creating codes, and the mathematics underlying the theory and practice of encryption and decryption.
“The puzzle nature of the course really appeals to students,” says Penelope Dunham, a research associate who offers the course. “Math majors and science majors love to solve puzzles.”
The course begins during the time of the Greeks and Romans with examples such as the Caesar cipher and proceeds all the way into the modern era. The Caesar cipher is a shift cipher, one of the simplest forms of encryption in which each letter of the message is replaced by a letter a certain number of positions down in the alphabet.
Some of the key moments in history that the class studies are the decoding of the Zimmerman Telegram in 1917 and the Allies’ successful cryptanalysis of Germany’s Enigma machine during World War II.
Intercepted and decoded by British intelligence, the Zimmerman Telegram was a secret diplomatic communication that proposed a military alliance of Germany, Mexico, and Japan in the event that the U.S. entered World War I. Its release inflamed U.S. public opinion and generated support for a declaration of war.
By World War II, the Germans were transmitting encrypted messages via the Enigma machine, but the British broke that as well. “Many students have seen the film The Imitation Game,” says Dunham, “but I think they’re still surprised to learn just how important the breaking of these codes has been throughout history.”
“The students really enjoy the first half of the course because it’s stuff they can break,” says Dunham. “When we get to things like the Enigma machine and the computer era, the students can no longer break the ciphers, so then it becomes more about learning the mathematics behind them.”
Today, thanks to the need to send data securely online, cryptography is an unseen part of everyday life, and students with the right math skills are in high demand.
“I’ve had two of my students go on to work for the National Security Agency, which is now one of the top employers of math Ph.D.’s in the world,” says Dunham.
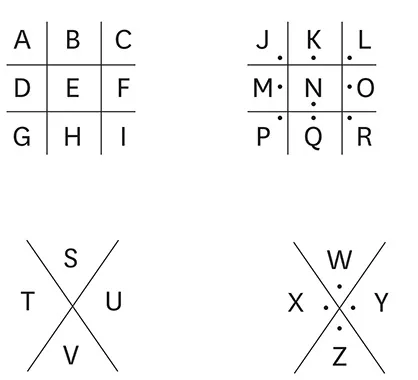
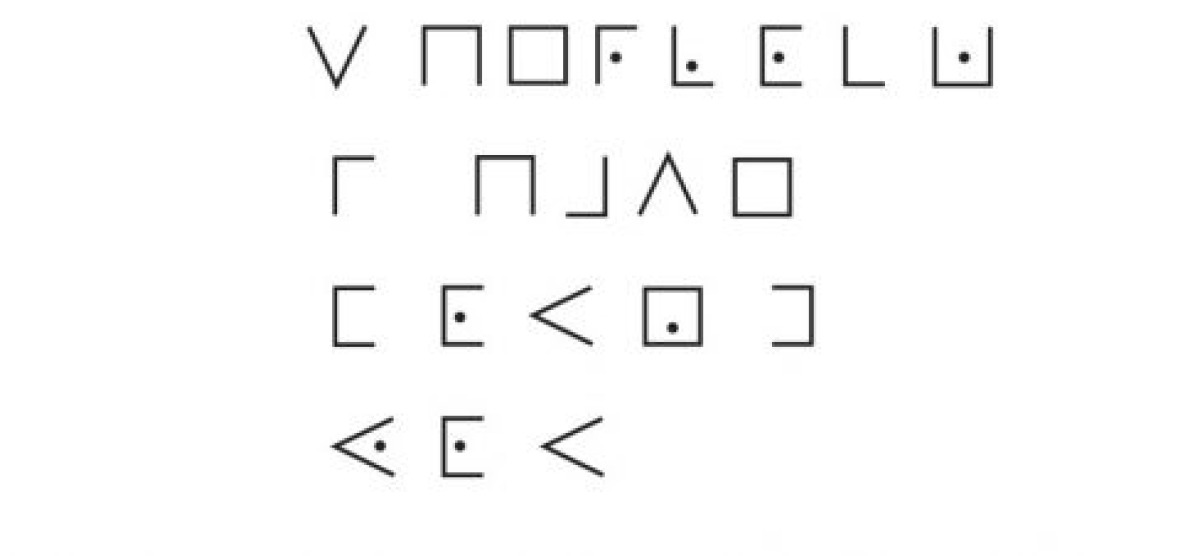
Above is the key to solving the puzzle at the top of the page. Scroll down for the correct answer.
Sherlock
I have
found
you
Ciphers vs. Codes
Codes substitute arbitrary symbols—typically, letters or numbers—for the components of the original message. Ciphers use algorithms to transform a message into an apparently random string of characters.
Et Tu?
The Caesar cipher is a shift cipher, one of the simplest forms of encryption in which each letter of the message is replaced by a letter a certain number of positions down in the alphabet.
Reading List
For history, students read Simon Singh’s The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography, and for math, Dunham assigns Cryptological Mathematics, by R.E. Lewand.
The Code Talkers
The name is generally associated with Navajos who served with Marine divisions in the Pacific. The Iwo Jima landing, for example, was directed entirely by Navajo code. But code talking had been pioneered during World War I by Cherokee and Choctaw Indians.
Published on: 05/13/2017